Azure Managed Application Installation Guide
Azure User Guide
Azure Manual Installation Guide
Azure VMWare Solution Quick Start Guide
Azure VMWare Solution Guide
Azure VMWare Solution Workflows
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Network Security Groups
Copy Markdown
Open in ChatGPT
Open in Claude
During deployment, we deploy a network security group on the VM level that includes the required inbound and outbound connections:
| Component | Management/Data NIC | Port (TCP) | Protocol | Notes |
|---|---|---|---|---|
| API Service | Management | 443 | HTTPS | API and lbcli |
| etcd Peer Port | Data | 2380 | TCP/IP | For etcd cluster peering |
| Lightbox Exporter | Management | 8090 | HTTP | Statistics and monitoring |
| Data Path | Data | 8009 | TCP/IP | NVMe/TCP data access |
| Discovery Service | Data | 4420 | TCP/IP | NVMe/TCP discovery access |
| Replicator Port | Data | 22226 | TCP/IP | Other nodes connect for replication to the node via this port. |
| SSH Connectivity | Management | 22 | SSH | Should be limited to specific origin ports. |
SSH connectivity is not mandatory and is required only if you use the lbcli on the storage VMs.
To add SSH port access to the NSG in the cluster's managed resource group:
- Click the created NSG in the managed resource group (for more, see the Managed Application section).
- Click the network security group.
- Click the inbound security rules.
- Click Add and add the SSH rules. You can also limit it for specific origin addresses.
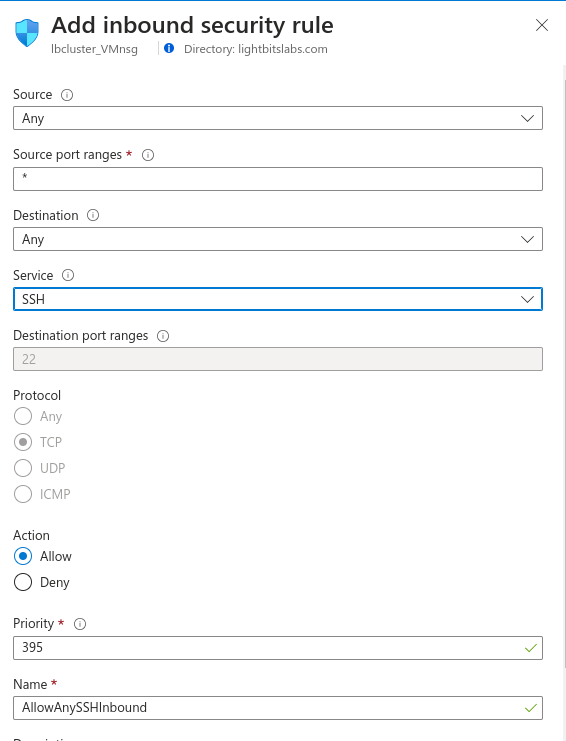
- Click Add. You should now see it in the list of rules.
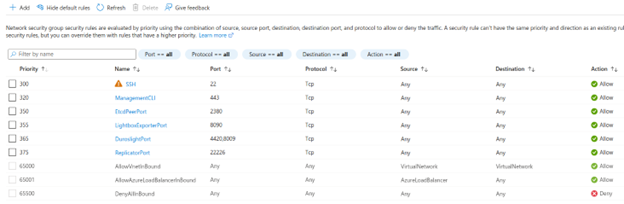
If you have a network security group or firewall rules set up on the Vnet/subnet, you will need to make sure that the following ports are open.
| Component | Management/Data NIC | Port (TCP) | Protocol | Notes |
|---|---|---|---|---|
| API Service | Management | 443 | HTTPS | API and lbcli |
| Statistics Exporter | Management | 8090 | HTTP | Statistics and monitoring |
| Data Path | Data | 4420,8009 | TCP/IP | NVMe client access |
| Outbound Internet | Azure API | 443 | HTTPS | Required outbound rule to the internet or to service tag AzureCloud. |
| SSH Connectivity | Management | 22 | SSH | Should be limited to specific origin ports. |
SSH connectivity is not mandatory and is required only if you use the lbcli on the storage VMs.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Access to the Cluster© 2026 Lightbits Labs™
Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message